A Message from Adamo’s CEO, Josh Godknecht Hello, security leaders. When I’m talking to security leaders, I’m talking to all of us. Whether your job is professional, vocational security enforcement of some sort, or you’re just a parent, friend or a spouse, a citizen at the grocery store, driving on the freeway, all of us have the responsibility for the well-being of our fellow citizen, our fellow … [Read more...] about How To Be An Effective Security Leader in Uncertain Times
How to Obtain a Facility Clearance (FCL)
A guide to navigating the facility security clearance process The facility clearance (FCL) process can be intimidating, as can all the acronyms you encounter along the way. But it’s relatively straightforward if you’re prepared. Follow the steps outlined below, and you’ll be on your way to having a cleared facility. How the Process Works Step 1: Secure a DD Form 254. The entire FCL process … [Read more...] about How to Obtain a Facility Clearance (FCL)
Keep Your Information Secure When Working From Home
Working from home with sensitive information can create a number of security risks, many of which are done unknowingly. Double-check that you are taking these precautions to keep your information secure. Secure your home WiFi network. Besides connecting to your own password-protected network, make sure that all of the devices connected to it—personal and family members’ devices—are all up to date … [Read more...] about Keep Your Information Secure When Working From Home
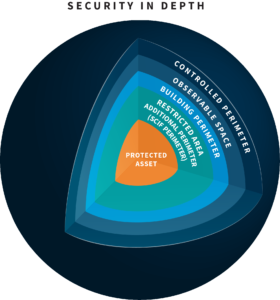
What is Security in Depth?
Security in Depth (SID) refers to the multiple layers of security used to safeguard an asset. These security measures function in concentric layers, much like an onion, utilizing a combination of different technologies and security operations to protect against physical threats and forced entries. At their best, these layers should deter, detect, delay and deny unauthorized … [Read more...] about What is Security in Depth?
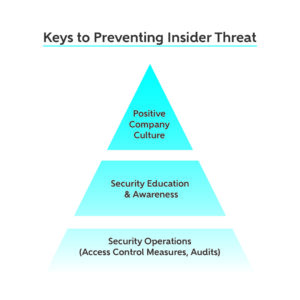
How to Prevent and Detect Insider Threat
Insider threat is the most persistent and prevalent type of security threat in the country. This type of threat occurs when an insider (an employee or contractor with authorized access) wittingly or unwittingly misuses their authorized access to negatively harm a company or organization. The risk of insider threat is high for any company or organization, governmental and non-governmental alike. … [Read more...] about How to Prevent and Detect Insider Threat
Awareness Tech Spec V1.5: Three Important Updates You Need to Know
Last week, the Office of the Director of National Intelligence released the long-awaited Version 1.5 of the “Technical Specifications for Construction and Management of Sensitive Compartmented Information Facilities,” commonly referred to as the “Tech Spec.” The document dictates how SCIFs/SAPFs are constructed both inside and outside the continental United States in order to earn government … [Read more...] about Awareness Tech Spec V1.5: Three Important Updates You Need to Know